

Enabling SAML affects all users who use this application, which means that users won't be able to sign in through their regular log in page. They'll only be able to access the app through the Okta service. However, Google Workspace users assigned to the Super Administrator role can bypass SSO and log in directly to https://admin.google.com. We highly recommend creating a Google Workspace Super Administrator account to allow for Google Workspace administrator access in the event SAML is no longer working properly.
The Okta/Google Workspace SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
In your Okta org's Google Workspace instance, the value of the RPID field on the Sign On tab determines which SSO profile is used.
If no value is specified for RPID, the root organization SSO profile is used.
If a value is specified for RPID, then a request for a multiple IdP profile is made using that value.
Sign in to Google Workspace with the same administrator username and password used for your Google Workspace user management API credentials in Okta.
Click the Security icon:

NOTE: If the Security icon is not visible, click More Controls at the bottom of the panel and drag the Security icon into the Admin Console dashboard.
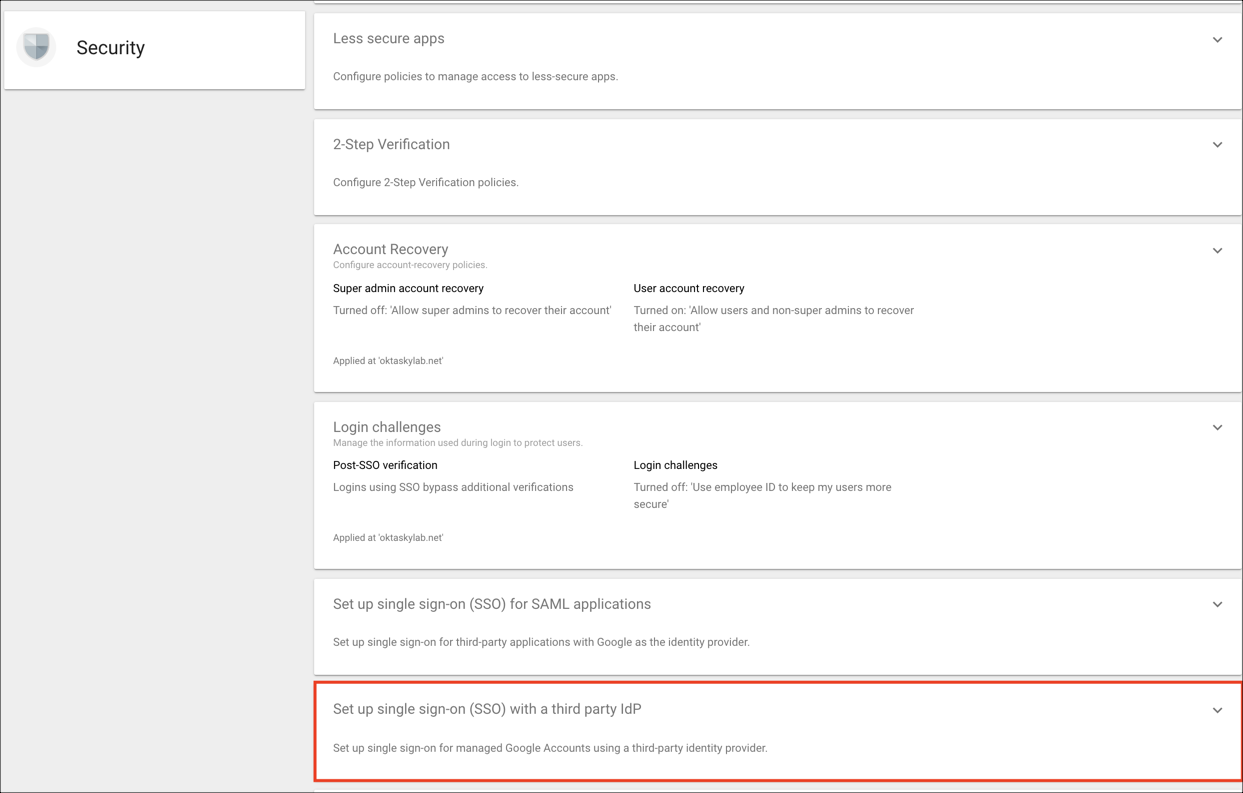
On the Security menu, select Set up single sign-on (SSO) with a third party IdP:
Follow the instructions for either:
Copy the following values as required when you configure an SSO profile in Google Workspace.
IDP entity ID:
Sign into the Okta Admin Dashboard to generate this variable.Sign-in page URL:
Sign into the Okta Admin dashboard to generate this value.
Sign-out page URL:
Sign into the Okta Admin dashboard to generate this value.
Verification certificate: Download and save the following file, then locate and upload it.
Sign into the Okta Admin Dashboard to generate this variable.
Change password URL:
Sign into the Okta Admin dashboard to generate this value.
Go to Third-party SSO profile for your organization and check Setup SSO with third party identity provider, and then enter the following:
Sign-in page URL: Copy and paste the value from SSO profile values.
Sign-out page URL: Copy and paste the value from SSO profile values.
Verification certificate: Copy and paste the value from SSO profile values.
Check Use a domain-specific issuer.
(Optional) Use the Network masks field to allow only a targeted subset of users to access your organization's Okta site. This is useful for rolling out application access in controlled phases.
Change password URL: Copy and paste the value from SSO profile values.
Click SAVE.
Done!
Your users are ready to single sign-on to Google Workspace!
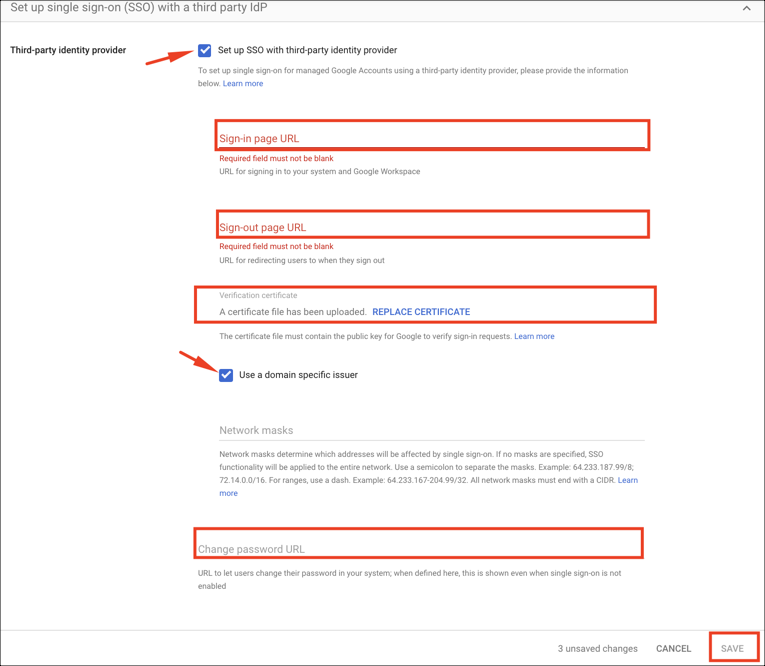
Go to Third-party SSO profiles, click Add SAML profile and then enter the following:
Enter a valid SSO profile name.
IDP entity ID: Copy and paste the value from SSO profile values.
Sign-in page URL:Copy and paste the value from SSO profile values.
Sign-out page URL: Copy and paste the value from SSO profile values.
Change password URL: Copy and paste the value from SSO profile values.
Verification certificate: Copy and paste the value from SSO profile values.
Click SAVE.
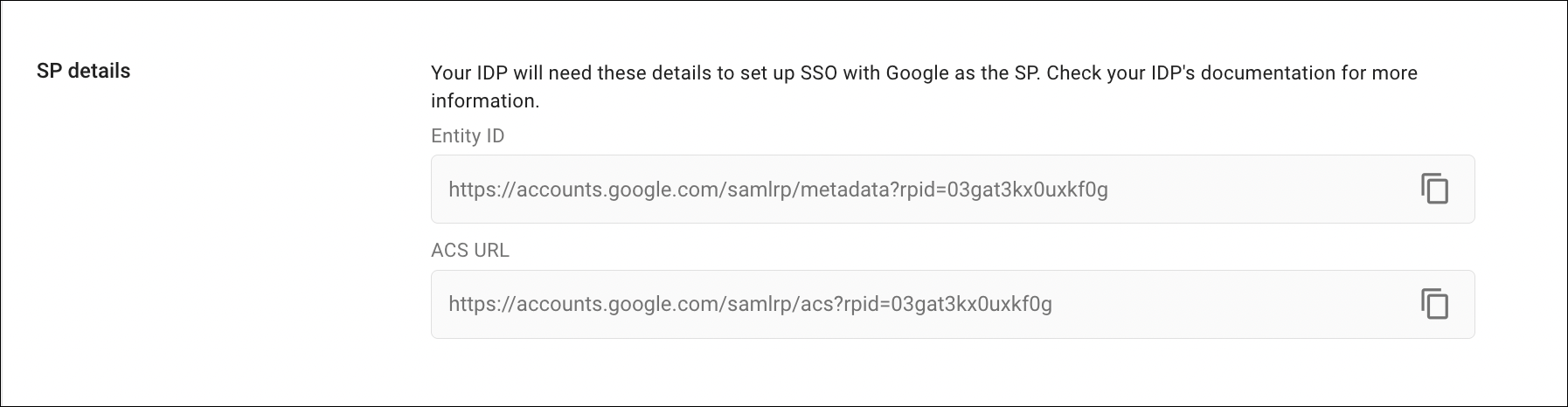
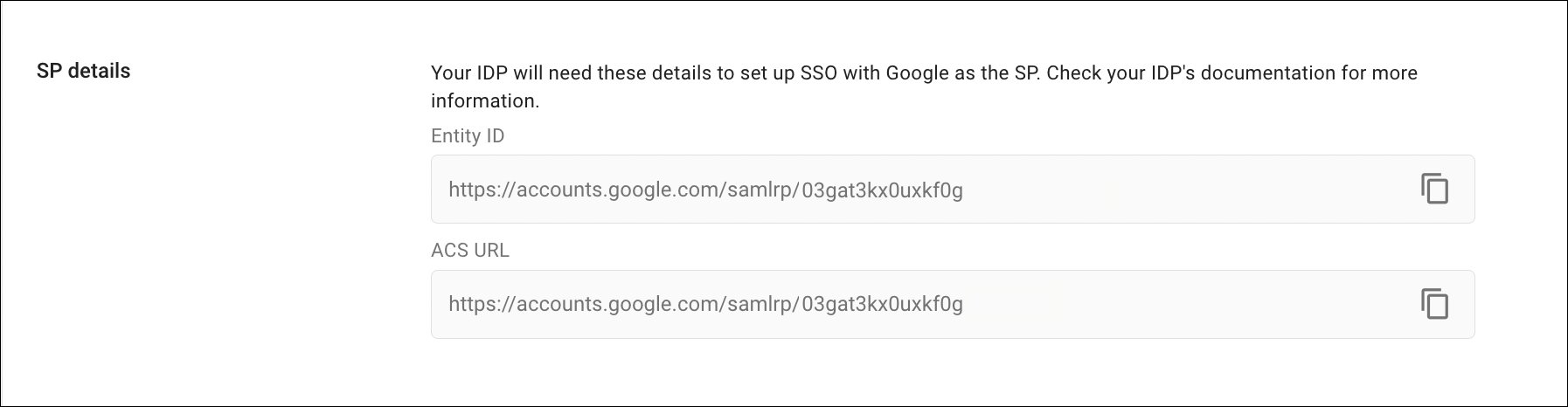
SP Details section: Copy the rpid value from Entity ID in the SP details section and use it as the RPID value on the Sign On tab of the the app instance in Okta. Depending on when you created your SAML SSO integration in Google, the format is either https://accounts.google.com/samlrp/metadata?rpid=rpid_value or https://accounts.google.com/samlrp/rpid_value.
The rpid value is 03gat3kx0uxkf0g in the following examples:
Done!
Your users are ready to single sign-on to Google Workspace!
Go to https://www.google.com/a/[DOMAIN]/ServiceLogin?continue=[SERVICE], where:
[DOMAIN] is your Google domain (the same value that you entered in Okta)
[SERVICE] is the Google service that you want to redirect to after authentication.
For example: https://www.google.com/a/acme.com/ServiceLogin?continue=https://mail.google.com.
Clear the Setup SSO with third party identity provider checkbox.
Delete any values from the Sign-in page URL, Sign-out page URL, and Change password URL fields. This ensures that users don't get redirected to Okta to login, as the Sign-in URL property is still enabled.