The Okta/Zscaler SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
Log into the ZScaler application.
Navigate to Administration > Authentication Settings:
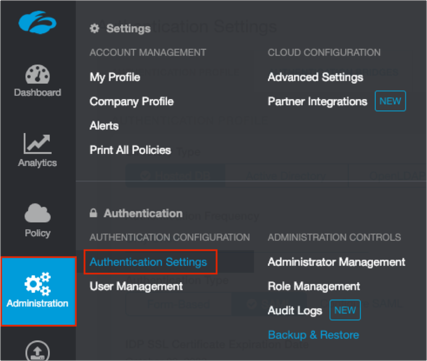
For Authentication Type, select SAML.
Click Configure SAML:
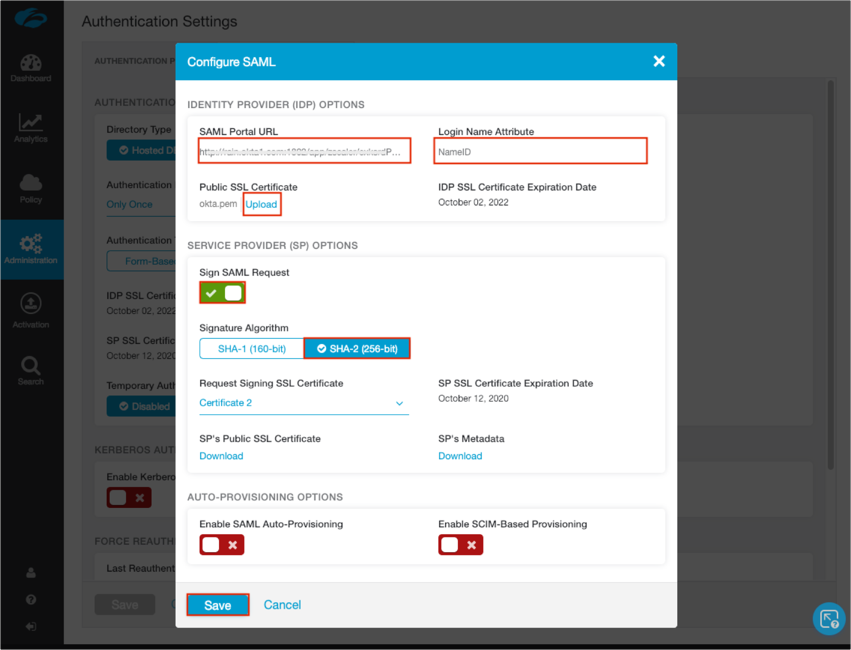
In the Identity Provider (IDP) Options section of the SAML Configuration screen, enter the following:
SAML Portal URL: Copy and paste the following:
Sign in to the Okta Admin app to have this variable generated for you.
Login Name Attribute: Enter NameID.
Public SSL Certificate: Download and save the following certificate for upload:
Sign in to the Okta Admin app to have this variable generated for you.
Then click Upload to upload it to Zscaler.
Sign SAML request: Activate.
Select SHA-2 (256-bit).
Click Save:
Done!
To setup a Auto-Provisioning on ZScaler, first setup Okta application integration:
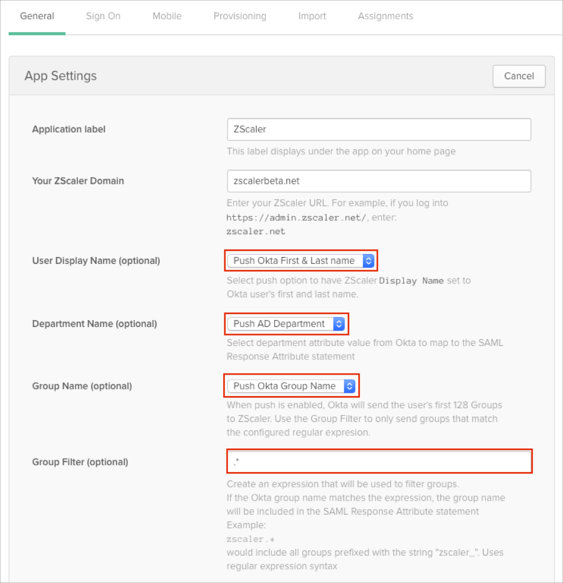
In Okta, on the General tab for ZScaler, click Edit, then enter following:
Select Display name mapping to Use. The user's display name, a concatenation of their first name and last name, is mapped to the attribute statement in the SAML Response.
Select Department mapping to AD Department.
The user's AD department is mapped to the attribute statement in the SAML Response
Select Group mapping to Use. User's groups is mapped to the attribute statement in the SAML Response.
Member of regular expression is used in conjunction with Group mapping.
The expression is used to filter groups. Groups that match the configured filter are mapped to the attribute statement in the SAML Response.
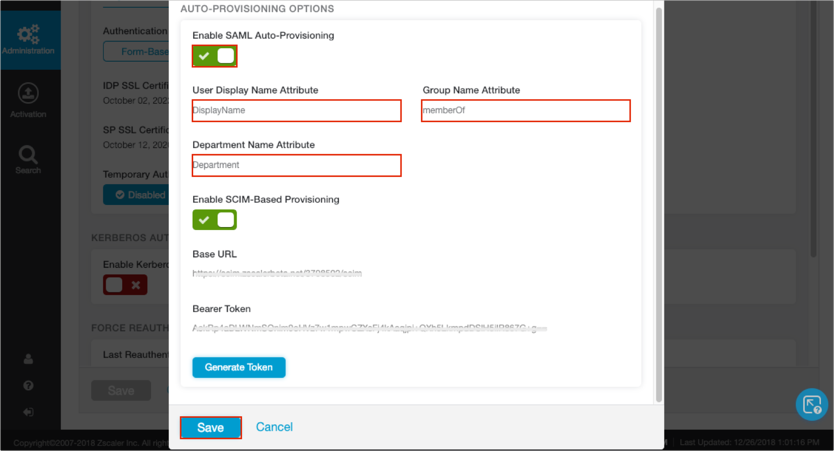
On the ZScaler Administration page, complete the following steps.
Click Manage Users & Authentication.
Click Edit, then click Configure SAML Single Sign-On parameters.
Click Enable SAML Auto-Provisioning.
For Attribute containing User Display Name enter the following:
DisplayName
For Attribute containing Group Name enter the following:
memberOf
For Attribute containing Department Name enter the following:
Department
Click Save:
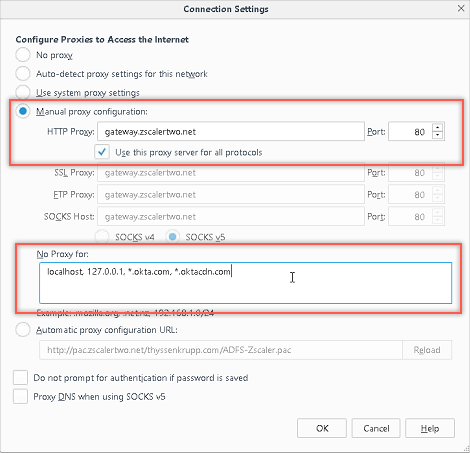
Set your browser proxy to gateway.[ yourZScalerDomain]:80.
For example if your ZScaler Domain is zscalerbeta.net; use gateway.zscalerbeta.net:80 proxy.
Add your Okta URL host ([yourSubdomain].okta.com) and *.oktacdn.com to the proxy bypass list.
For example if you log into https://acme.okta.com/; enter acme.okta.com.
Here is an example, shown in a Firefox browser:
Your users are ready to single sign-on to ZScaler.
Make sure that you entered the correct value in the Your ZScaler Domain field under the General tab in Okta. Using the wrong value will prevent you from authenticating via SAML to ZScaler.
The following SAML attributes are supported:
| Name | Value |
|---|---|
| DisplayName, Department, memberOf | This is configured in the app UI; see Setup Active Directory integration with ZScaler for Auto-Provisioning instructions above. |
Enter your User Name, then click Sign In: