NOTE
This Okta app is only to be used for adding authentication to Sigma on GCP.
If you are using Sigma on AWS, you need to set up a custom SAML app in Okta using the configuration values listed in Sigma's documentation
The Okta/Sigma on GCP SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
Sign in to Sigma as an Organization Admin.
Click your icon, then select Administration:
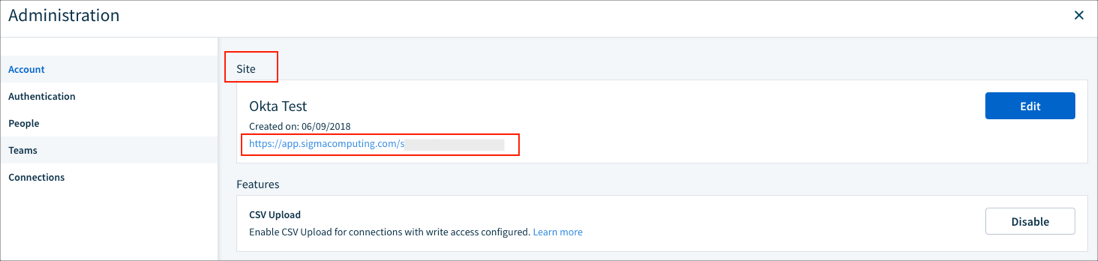
In the Site section make a copy of your Company Login URL (this value is needed for SP-initiated SSO and IdP-initiated SSO), then go to Authentication:
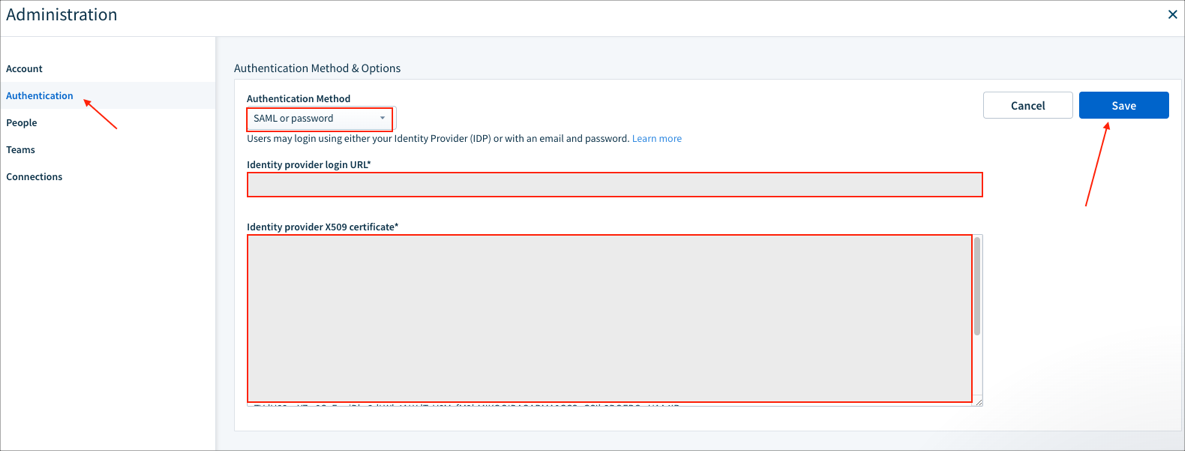
Go to Authentication, click Edit, then enter the following:
Authentication Method: Select either SAML (Users may login using either your Identity Provider (IDP or with an email and password), or SAML or password (Users must login using your Identity Provider (IDP).
Identity Provider Login URL: Copy and paste the following:
Sign in to the Okta Admin app to generate this variable.
Identity Provider X509Certificate: Copy and paste the following:
Sign into the Okta Admin Dashboard to generate this variable.
Click Save:
In Okta, select the Sign On tab for the Sigma on GCP app, then click Edit:
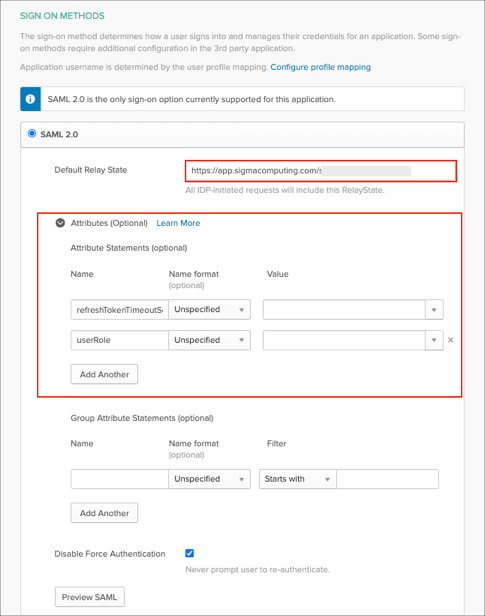
Default Relay State: Enter your Company Login URL you made a copy of in step 3.
SAML Attributes (optional):
By default Okta supports only firstName and lastName SAML attributes that are mandatory for JIT. You can configure additional attributes and their values (mappings) under the Attributes (Optional) section of SAML.
The following optional attributes are supported by Sigma: refreshTokenTimeoutSecs, userRole.
Note: The value for refreshTokenTimeoutSecs can be any positive integer. The value for userRole should be one of admin, author, or viewer.
Here is an example of the configuration for the additional attributes:
Note: You can add the groups attribute in the Group Attribute Statements (optional) section and specify a required filter in order to send Okta groups to the Sigma instance.
Click Save:
Done!
The following SAML attributes are supported:
| Name | Value |
|---|---|
| firstName | user.firstName |
| lastName | user.lastName |
Optional attributes:
| Name | Value |
|---|---|
| refreshTokenTimeoutSecs | See step 5 to configure optional attributes and their values (mappings) |
| userRole | See step 5 to configure optional attributes and their values (mappings) |
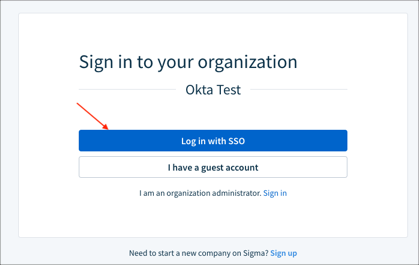
Go to your Company Login URL you made a copy of in step 3.
Click Log in with SSO: