The Okta/BMC Remedyforce SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
Login to your BMC Remedyforce account as an administrator.
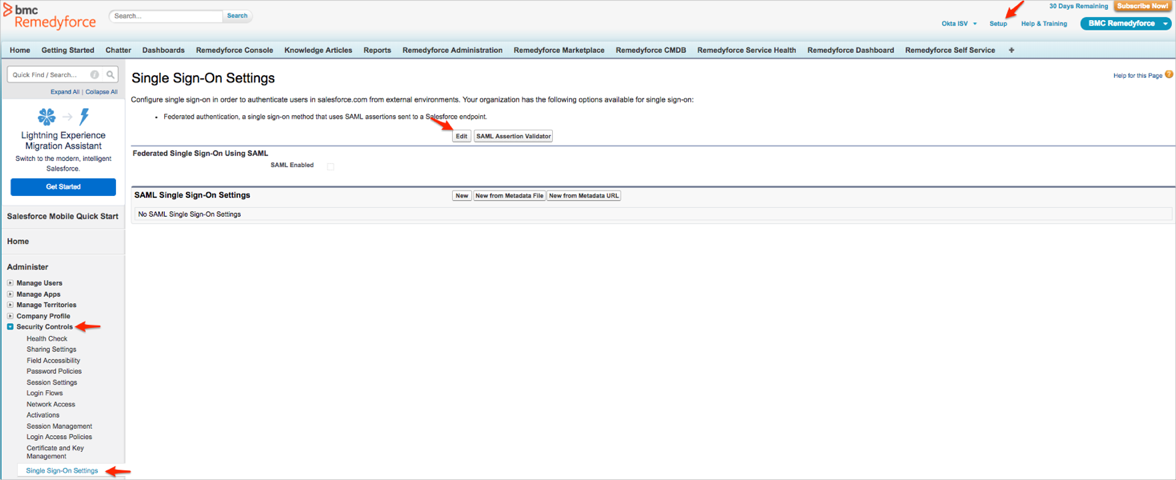
Navigate to Setup > Security Controls > Single Sign-On Settings, then click Edit:
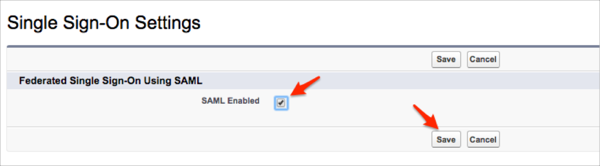
Select the SAML Enabled checkbox then click Save:
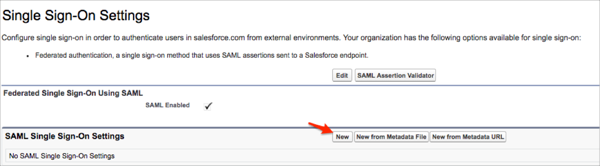
Click New:
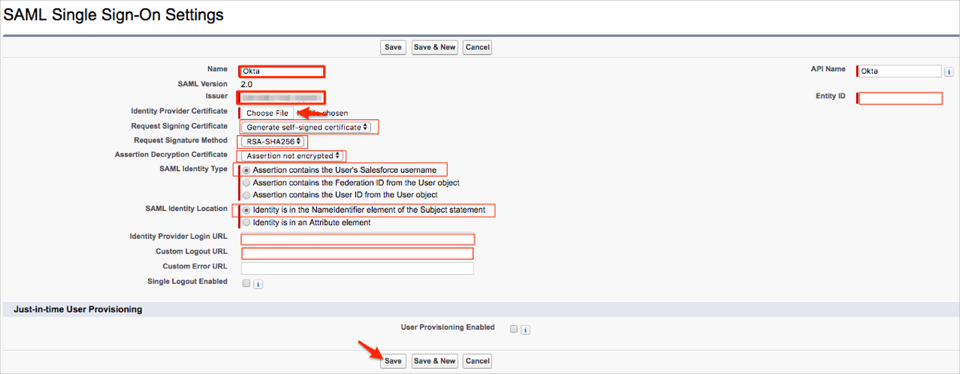
Follow the steps below:
Name: Enter a preferred name.
Issuer: Copy and paste the following:
Sign into the Okta Admin dashboard to generate this value
Sign in to the Okta Admin dashboard to generate this value.
Request Signing Certificate: Select Generate self-signed certificate.
Request Signing Method: Select RSA-SHA256.
Assertion Decryption Certificate: Select Assertion not encrypted.
SAML Identity Type: Select Assertion contains the User's Salesforce username.
SAML Identity Location: Select Identity is in the Nameidentifier element of the Subject statement.
Sign into the Okta Admin dashboard to generate this value
Custom Logout URL: Copy and paste the following:
Sign into the Okta Admin dashboard to generate this value
https://saml.salesforce.com
Click Save.
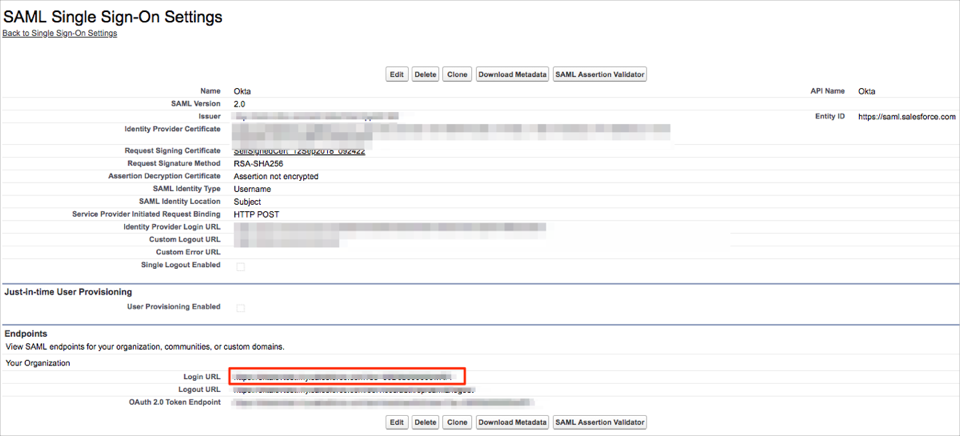
Still on the SAML Single Sign-On Settings page, copy your Login URL value:
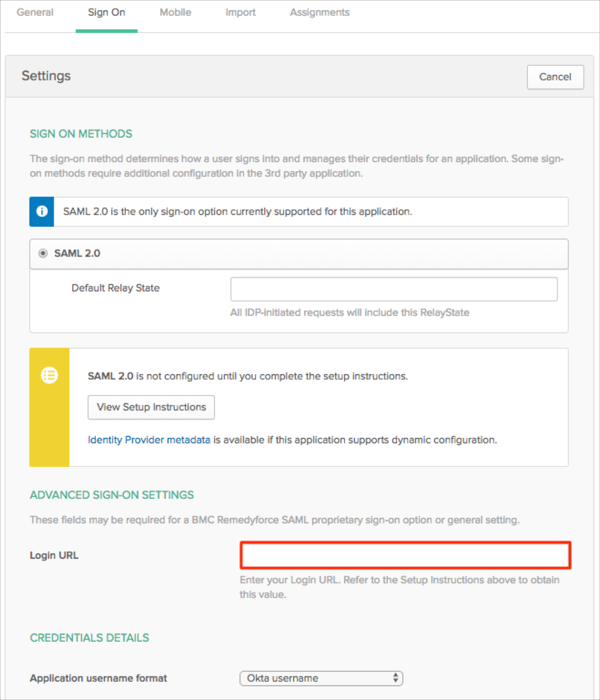
In Okta, select the Sign On tab for the BMC Remedyforce app, then click Edit.
Enter the Login URL value you made a copy of in step 6 above into the corresponding field.
Click Save:
Done!
Navigate to your Salesforce Domain URL. You should see an option to login using your Identity Provider: