

Read this before you enable SAML
Enabling SAML will affect all users who use this application, which means that users will not be able to sign in through their regular sign-in page. They will be able to access the app through the Okta service.
Backup URL
Amazon Managed Grafana doesn't provide a backup sign-in URL where users can sign in using their regular username and password. However, users can disable SAML from their console.
The Okta/Amazon Managed Grafana SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
Sign in to your AWS console, then navigate to Amazon Managed Grafana.
On right side, click Create Workspace.
On the Create New Workspace page enter a Workspace name and optional Workspace description, then click Next.
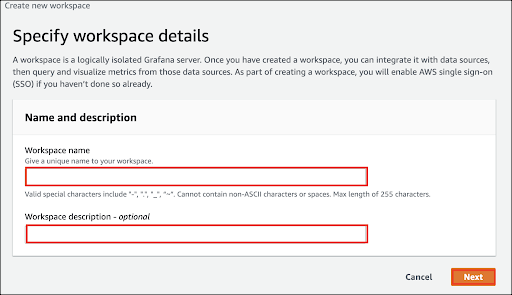
On the Configure Settings page, select Security Assertion Markup Language (SAML), as the authentication method, and Service Managed as the Permission type, then click Next.
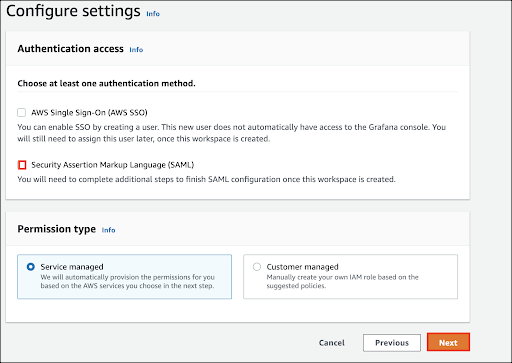
On the IAM permission access settings page, keep the default settings, then click Next.
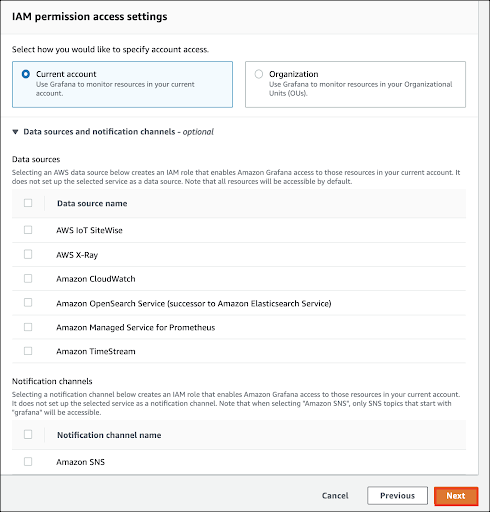
Click Create workspace.
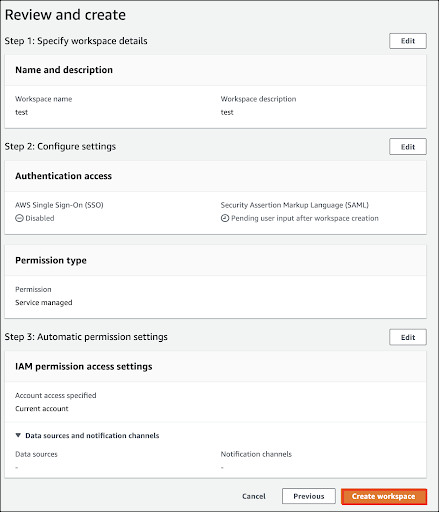
On the Workspace page, click SAML Configuration.
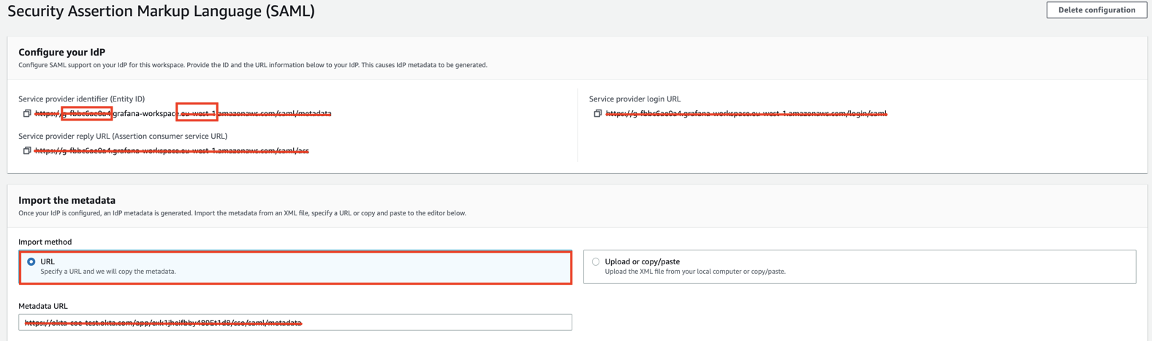
Enter the following:
Service provider identifier (Entity ID: Make a copy of the Name Space and Region values.
https://[namespace].grafana-workspace.[region].amazonaws.com/saml/metadata.
Import the metadata: Select URL as the Import method, then copy and paste the following Metadata URL:
Sign into the Okta Admin dashboard to generate this value.
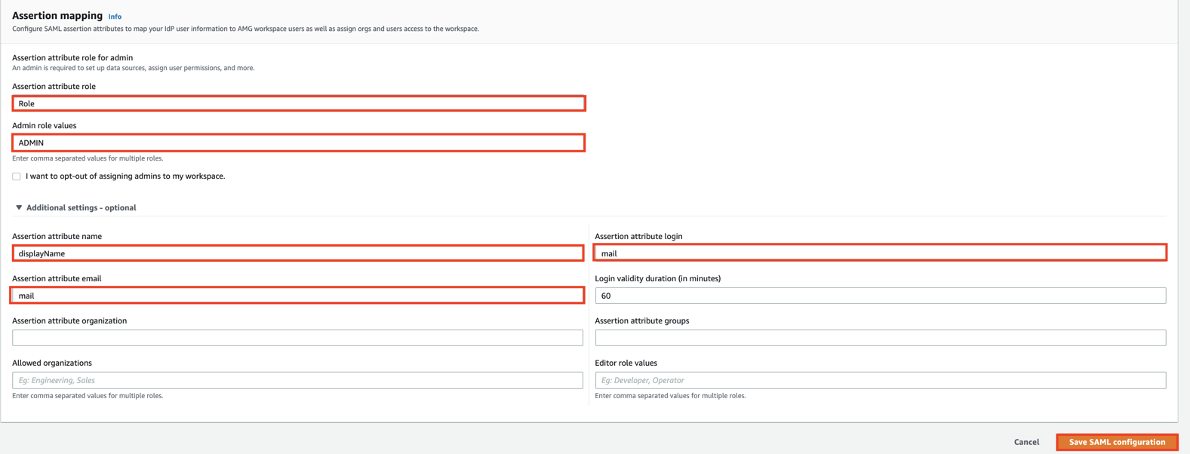
Assertion Mapping (Optional). See Notes for details.
Assertion attribute role: Enter Role
Admin role values: Enter ADMIN
Under Additional settings - optional, enter the following:
Assertion attribute name: displayName
Assertion attribute login: mail
Assertion attribute email: mail
Click Save SAML configuration.
In Okta, select the Single Sign on tab for the Amazon Managed Grafana SAML app, then click Edit and enter the following:
Name Space: Enter your Name Space (step 8).
Region: Please Enter your Region (step 8).
Click Save.
Done!
Enter your Email Address, then click Login.
AWS expects to receive in the assertion the attributes mail and displayName with their corresponding values.
For example: johndoe@acme.com and John Doe.
If you decide to send a different attribute, make sure you update the relevant fields in AWS. For example, the Assertion attribute.
Amazon Managed Grafana uses JIT provisioning and authorization, which means it relies on certain attributes keys and value to be sent as part of the assertion, in the example in step 8 the attribute Role and value ADMIN are set, which means that every user who has this attribute and value will have an administrator privileges in the Amazon Grafana workspace.