The Okta/HighBond SAML integration currently supports the following features:
For more information on the listed features, visit the Okta Glossary.
Login to your ACL account as an administrator.
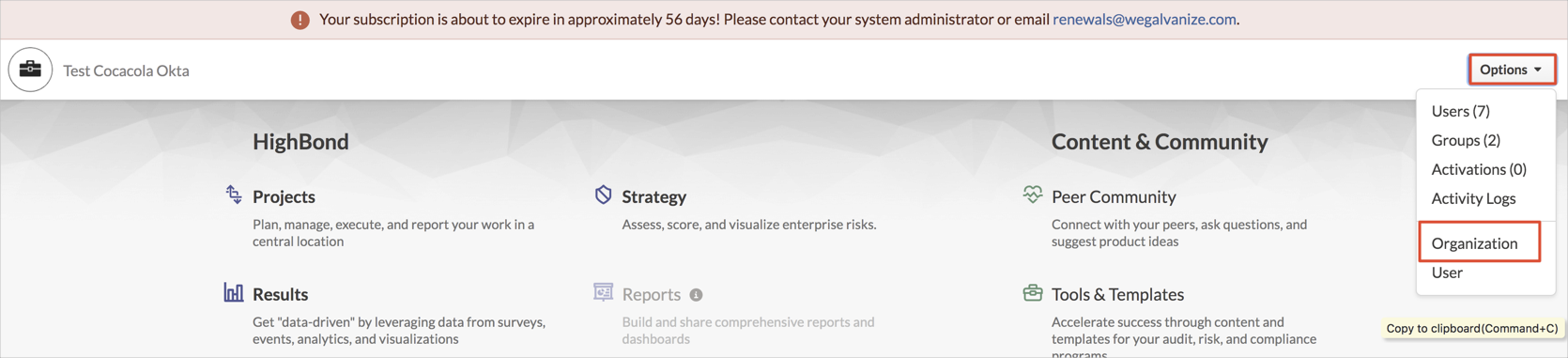
Click on the Options drop down, then select Organization:
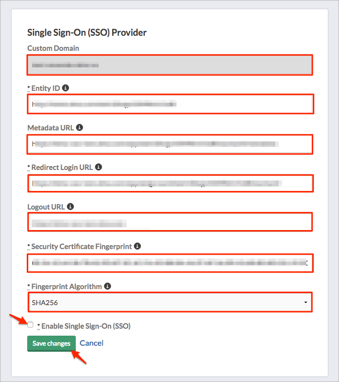
In the Single Sign-On (SSO) Provider section, select Manage SSO Settings:

Follow the steps below:
Sign into the Okta Admin Dashboard to generate this variable.
Sign into the Okta Admin dashboard to generate this value.
Sign in to the Okta Admin app to generate this variable.
Sign into the Okta Admin Dashboard to generate this variable.
Sign into the Okta Admin dashboard to generate this value.
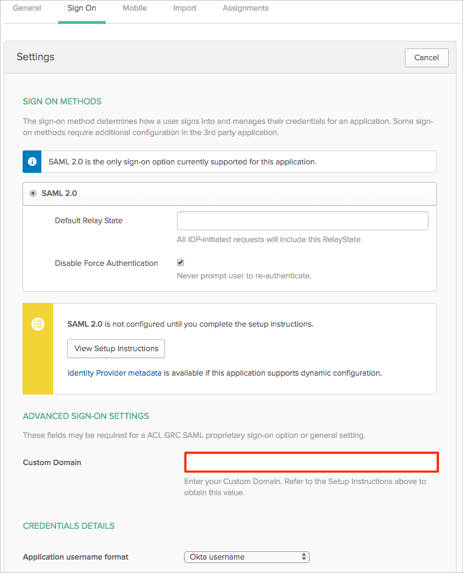
In Okta, select the Sign On tab for the ACL GRC SAML app, then click Edit:
Enter the Custom Domain value you made a copy of in step 3 into the corresponding field.
Click Save.
Done!
The following SAML attributes are supported:
| Name | Value |
|---|---|
| name | user.firstName user.lastName |
Click Sign in to a custom domain:
Enter your custom domain, then click CONTINUE: