

The Okta/Symantec Web Security Service SAML integration currently supports the following feature:
Copy and save the following as metadata.xml:
Sign in to Okta Admin app to have this variable generated for you.
Sign in to your Symantec Web Security Service instance as an administrator.
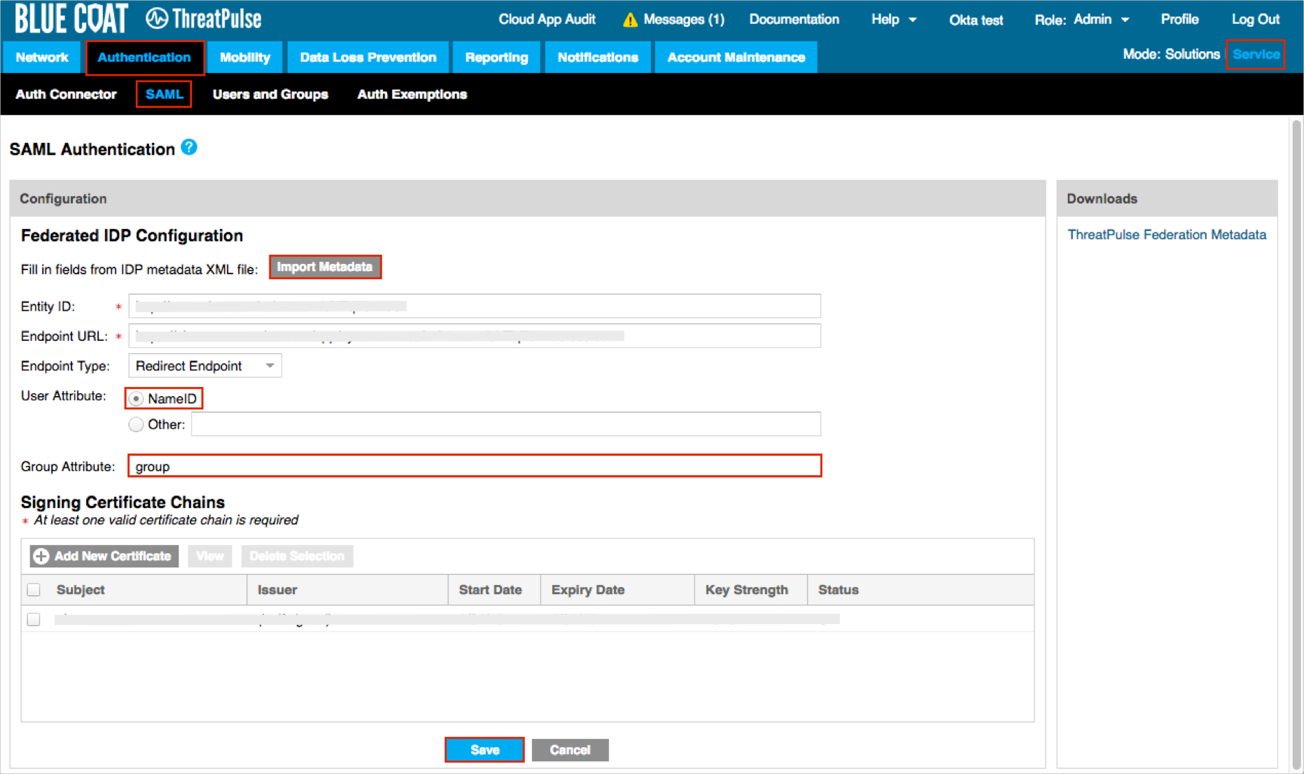
Navigate to Service > Authentication > SAML, then enter the following (see screen shot at end of step for reference):
Click Import Metadata to locate and upload the metadata.xml file you saved in step 1.
User Attribute: Select NameID.
Group Attribute: Enter group.
Click Save.
Navigate to Network > Locations, then click Add Location:
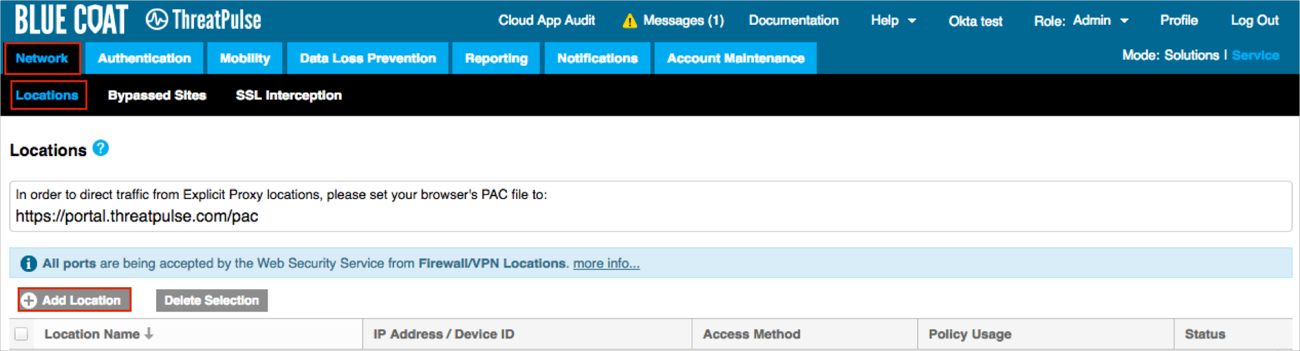
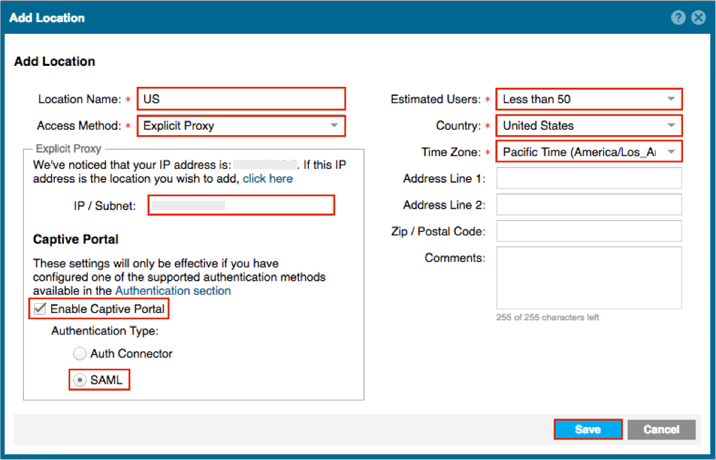
Enter the following (see screen shot at end of step for reference):
Location Name: Enter a name. We used US in our example.
Select an Access Method. We used Explicit Proxy in our example.
Enter your IP/Subnet value.
Check Enable Captive Portal.
Authentication Type: Select SAML.
Select one of the options for Estimated Users.
Select your Country.
Select your Time Zone.
Click Save.
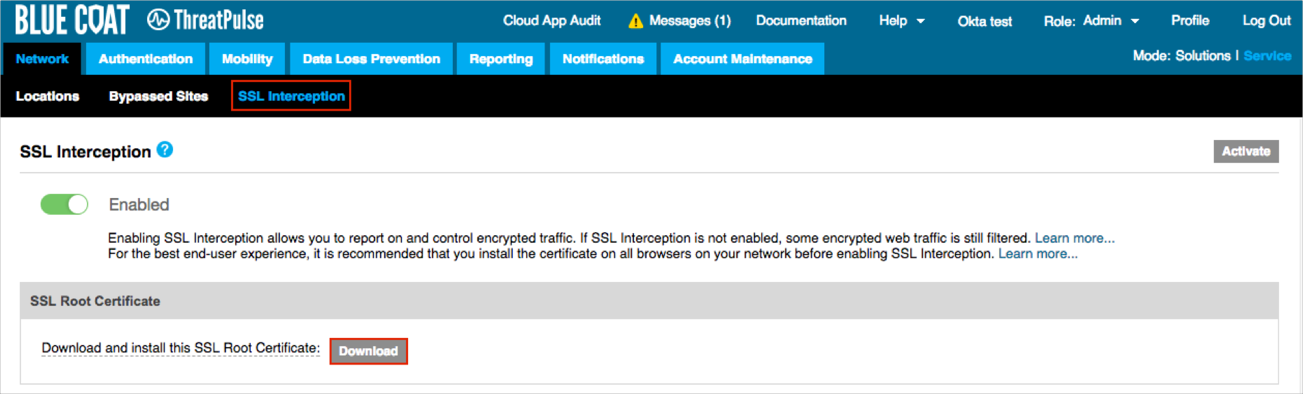
Select the SSL Interception tab.
Click Download to download then install the SSL Root Certificate:
In order to pass Okta groups as part of the SAML Response:
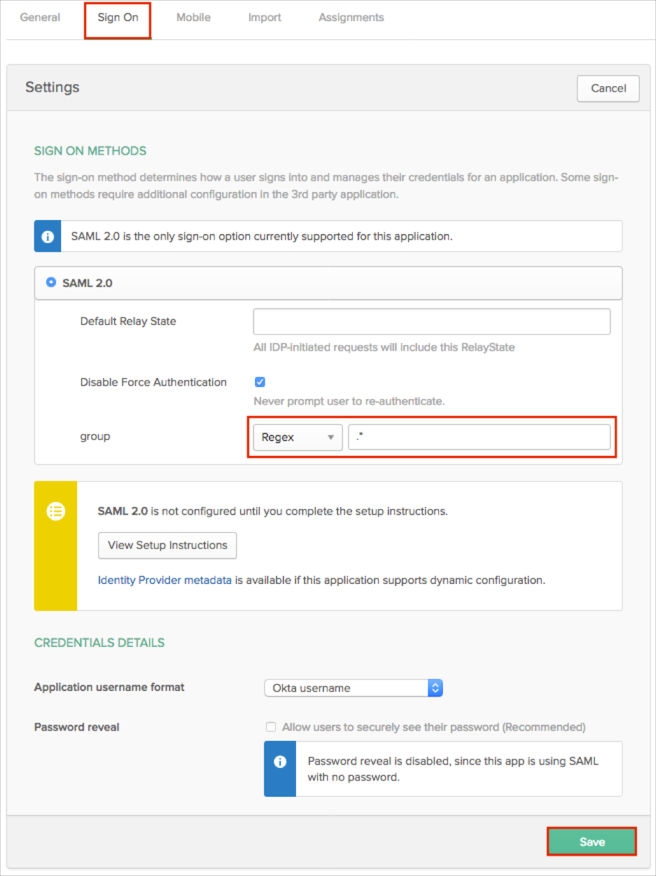
In Okta, select the Sign On tab for the Symantec Web Security Service app, then click Edit.
Select your preferred group filter from the dropdown list (the Regex rule with the value ".*" in order to send *all* groups to the Symantec Web Security Service instance we used in our example).
Click Save.
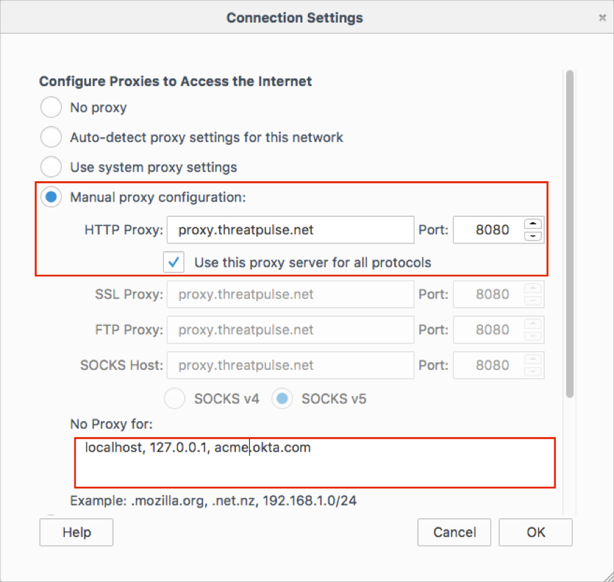
Set your browser proxy to proxy.threatpulse.net:8080.
Add your Okta URL host ([yourSubdomain].okta.com) to the proxy bypass list.
For example if you log into https://acme.okta.com/; enter acme.okta.com.
Here is an example, shown in a Firefox browser:
Done!
The following SAML attribute is supported:
| Name | Value |
|---|---|
| group | This will be configured in the app UI; see group attribute instructions (step 8) above. |
Open a required site in your browser.